Coevolve’s Remote Access Solution
A rapid-deployment capability
Coevolve’s Remote Access Solution is a rapid-deployment capability to provide effective and secure connectivity for remote workers.
Legacy solutions present a DC-centric architecture by which a VPN concentrator appliance is deployed in a nominated data center or HQ office to act as an entry point for the internal network resources. Regardless of whether the user and the destination application are located, the same appliance is always used to place users ‘in the network’ and this can quickly result in suboptimal routing and significant poor application performance. Coevolve’s Remote Access Solution is a rapid-deployment capability specifically scoped to provide a quick answer to current challenges experienced by network and security administrators in providing effective and secure connectivity for remote workers.
Underlying technology
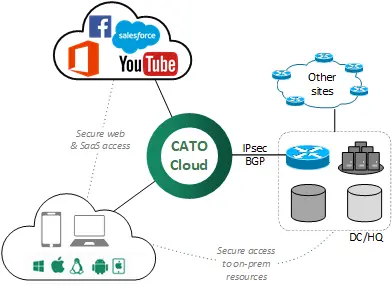
Coevolve’s Remote Access Solution is based on Cato Networks Remote Access technology. The Cato Cloud leverages 50+ PoPs distributed worldwide, meshed via a guaranteed private backbone. Cato clients connect automatically to the closest / best POP to leverage the private backbone and thus connect to both on-prem and SaaS / cloud destinations.
Additionally, the platform provides embedded security features such as NG-Firewall, URL filtering, Anti-Malware and IPS/IDS engines. A robust set of default security policies are available straight out-of-the-box, yet these can also be further customized via an intuitive admin web portal (CC2).
Onboarding Process
The solution has been architected with simplicity in mind, ultimately resulting in short implementation times with as little as three steps required:
- Provision IPsec tunnel between a Cato PoP and a nominated customer site such as a data center or HQ office
- Install the Cato Remote Client. This can either be done by end users upon invitation from CC2 or pushed as a Group Policy Object
- Provision routing and security rules
Requirements
Customer environments are required to have an IPsec-capable device in their nominated location. This can be an existing firewall or router. Both IKEv1 and IKEv2 are supported. It is also recommended to run BGP over the IPsec tunnel in order to simplify the subsequent routing configuration, but the option of doing this or rely on static routing can be further assessed on a case by case basis.
Next steps
Please contact us to learn more about this solution and how we can help provide high-performance remote access for your users!